A checksum is a price that represents the number of bits in a transmission message. IT professionals use it to detect high-level errors inside data transmissions. Earlier to transmission, each bit of information or file could possibly be assigned a checksum price after working a cryptographic hash carry out. The time interval checksum will also be typically substituted with the phrases hash sum or hash value.
Why apply checksums
The primary intention of calculating checksums is to detect changes throughout the data. These changes is prone to be the outcomes of error or manipulation. Regardless of the set off, a checksum that’s calculated using a checksum algorithm produces a fixed-size string or amount that allows clients to verify the integrity of the despatched data and guarantee that it has not been altered or tampered with all through transmission.
Apart from malicious tampering, data integrity may also be affected on account of unintended errors. These errors is prone to be launched all through data transmission or data storage. Checksums can help clients to detect these errors. They try this by calculating the checksum of the acquired data and evaluating it to the checksum provided from the distinctive data set. If there is a distinction, they’re going to take acceptable movement. As an example, they’re going to re-download the file or ask the sender to resend the message.
How checksums work
Checksums work by giving the celebration on the receiving end particulars in regards to the transmission to guarantee that the whole differ of information is delivered. The checksum price itself is unique — normally an prolonged string of letters and numbers. It is calculated from the information object and appended to the despatched packet.
On the sender’s end, a checksum generator makes use of a checksum algorithm to calculate the checksum price from the information object that is perhaps despatched to the recipient. The generator divides the information object into equal subunits of n-bit measurement (usually 16 bits) and supplies the subunits using one’s complement methodology to achieve at a sum of n bits. This complemented sum price (checksum) is added to the highest of the distinctive data object and transmitted with it. It acts as a sort of fingerprint for a file or set of recordsdata to level the number of bits included throughout the transmission.
The individual on the receiving end moreover calculates the checksum price, this time using a checksum checker. If this price is even barely completely completely different (non-zero) from the checksum price of the distinctive file, it could nicely alert all occasions throughout the transmission that the file was corrupted or most likely tampered with by a third celebration, equal to throughout the case of malware. From there, the receiver can study what went flawed or try downloading the file as soon as extra.
Recommendations on learn how to calculate checksums
The very best technique to calculate a checksum is to do the subsequent:
- Add the entire byte values in a message.
- Use the least-significant byte of the sum as a result of the checksum byte.
Two important operations utilized in checksum calculations are sum and shift.
Ponder two hexadecimal digits of the checksum P1 and P2.
If i represents the increment and if H(i) denotes the shift of digit i, that is how the checksum is perhaps calculated for the two hex digits P1 and P2:
- Start with i = 0
- Start with P1 = 0 and P2 = 0.
- Let P1 = P1 + D(i + 1) #Sum.
- Let P2 = P2 + D(i + 2) #Sum.
- Let P1 = H(P1).
- Let P2 = H(P2).
- Let i = i + 2.
- Is i < 32? Then return to steps 2 and three and repeat; in every other case, go to step 9.
- P1 is the first checksum digit, P2 is the second checksum digit.
The frequent protocols used to seek out out checksum numbers are Transmission Administration Protocol (TCP) and Particular person Datagram Protocol (UDP). TCP is normally additional reliable for monitoring transmitted packets of information, nevertheless UDP is prone to be helpful to steer clear of slowing down transmission.
Advantages of checksum
A main checksum algorithm is sufficient to verify data integrity and authenticity in fairly a number of applications, and it could nicely detect if any malicious tampering or unintended errors have occurred as the information is being transmitted using public/private networks, clouds or arduous drives. Checksums current an early warning to cease data losses on account of sudden or unintended events like viruses, malware or deliberate corruption makes an try. Moreover they current a technique for patrons to detect incomplete data transfers, which might consequence on account of unintended file edits or deletions.
Checksums are moreover useful all through data storage. As an example, data saved in shared drives and accessed by a variety of people by means of the internet is prone to be inadvertently modified or maliciously tampered with. It may also be duplicated, with completely completely different recordsdata containing the an identical data saved in a number of locations. Making use of a checksum can help detect such events and thus improve accountability throughout the system. Moreover, if the information is saved over prolonged intervals, checksums are useful to verify its security and authenticity.
Lastly, checksums are helpful to create data inventories for archival features. The archived data is probably not in vigorous use or it’s prone to be ingested from old-fashioned storage devices (CDs, cassettes, and plenty of others.). By calculating a novel string of characters from an data file , the integrity of that file could possibly be verified, thus guaranteeing that data was not corrupted by the change.
Disadvantages of checksum
Whereas checksums are useful for detecting transmission errors or data manipulation, they can not detect all errors. Such restricted detection performance implies that errors like byte rearrangements (bytes throughout the flawed order), missing bytes, or zero-value bytes could possibly be missed, resulting in lack of expertise integrity and incorrect communications even when checksums are used.
Moreover, checksums mustn’t basically essentially the most reliable methodology to protected data transmissions. The values could possibly be manipulated or stable by malicious occasions. These actors may also use refined methods to compromise data, rendering checksums inadequate for guaranteeing data integrity.
One different drawback: Checksums can solely detect errors. There isn’t any such factor as a built-in mechanism to restore the errors and recuperate corrupted data. Lastly, checksum calculations add complexity and overhead to the information change course of.
Checksum functions and use circumstances
Data integrity verification is important for lots of functions. Because of considered one of many important features of checksum is to verify data integrity, this system is normally used for the subsequent:
- Group communications.
- Cybersecurity (to verify data confidentiality, integrity and availability — additionally referred to as the CIA Triad).
- Data storage and archival.
- Verification of log files.
- Software program program distribution and updates.
- Know Your Purchaser (KYC) verifications (e.g., in banking).
- E-commerce product availability checks.
- Bill price verification.
- Verification and communication of check out results in healthcare.
What might trigger an inconsistent checksum amount?
Whereas checksum values that don’t match can signal one factor went flawed all through transmission, a few elements might trigger this to happen, equal to the subsequent:
- An interruption throughout the net or group connection.
- Storage or home factors, along with points with the hard drive.
- A corrupted disk or corrupted file.
- A third celebration interfering with the change of information.
All of the above events can result in the alteration of information all through transmission, resulting in a definite checksum than the distinctive. Nonetheless, not the entire incidents level out data tampering or finish in data losses.
Widespread types of checksum algorithms
There are a variety of cryptographic hash capabilities which may be or have been used to generate checksum values. Only a few frequent ones embody the subsequent:
- Secure Hash Algorithm (SHA) 0. This hash carry out, created in 1993, was the first of its type. It produced a 160-bit output that acted as a “fingerprint” of the enter. Nonetheless, it was withdrawn in 1996 after the NIST discovered that its “collision security energy” is significantly lower than a terrific hash carry out, making it inclined to many types of cyberattacks.
- SHA-1. SHA-1 was first printed in 1996. Like SHA-0, it generates an output hash price of 160 bits. By 2010, this hash carry out was not thought-about protected. The NIST moreover actually useful that the algorithm not be used for producing digital signatures or to protect delicate information after Dec. 31, 2010.
- SHA-2 (SHA-224, SHA-256, SHA-384, SHA-512). This family of hash capabilities is dependent upon the size of the file and numbers to create a checksum price. An enchancment as compared with SHA-0 and SHA-1, each algorithm from this family has a definite hash measurement, which inherently means a definite stage of security. This explains why SHA-2 has been utilized in numerous security protocols, along with Transport Layer Security, Secure Sockets Layer and IPSec. Even so, the following checksums are weak to measurement extension assaults, which comprise a hacker reconstructing the inside state of a file by learning its hash digest. Moreover, some older functions and dealing packages do not help SHA-2, creating compatibility factors that set off disruptions and impact individual experiences.
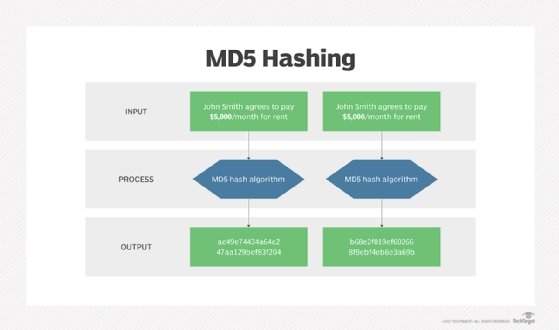
- Message Digest 5 (MD5). The MD5 hash carry out creates a checksum price, nevertheless each file won’t basically have a novel amount. So, it’s open to vulnerabilities if a hacker swaps out a file with the an identical checksum price (typically referred to as a collision assault). Because of this MD5 is just acceptable to confirm for corruption in a file. It is not advisable to rely upon this hash carry out to verify the file’s authenticity.
Recommendations on learn how to confirm an MD5 checksum
To verify {{that a}} file hasn’t been tampered with, the MD5 hash of that file must be confirmed. Moreover, when placing in drivers or patches, it’s important to ensure that the downloaded files are complete.
The MD5 hash is a cryptographic checksum which may be checked on each a PC or laptop computer laptop. It should even be verified on completely completely different working packages, equal to Microsoft Residence home windows, Linux and Apple macOS.

Verifying an MD5 checksum on Residence home windows
- Open Residence home windows PowerShell or the command line by clicking on the Residence home windows button on the Start menu.
- As quickly as on the command prompt, type cmd throughout the search subject, and press Enter. Alternatively, press the Residence home windows button and R, type cmd, and press Enter.
- Go to the folder that comes with the file whose MD5 checksum should be verified by typing cd adopted by the path to the folder that the file resides in. Alternatively, the required folder could possibly be dragged and dropped from Windows Explorer to insert the path.
- Sort certutil -hashfile MD5. Substitute with the file establish.
- Press Enter.
The outcomes of the checksum could possibly be in distinction and verified with the anticipated outcomes.
Verifying the MD5 checksum on a Mac
- Open Terminal.
- Navigate to the folder that comes with the file whose MD5 checksum needs verification. Alternatively, for direct route, Terminal could possibly be open correct at a folder from Finder.
- Sort md5 , and alter with the file establish. Alternatively, the file will even be dragged and dropped into the Terminal window after typing md5.
- Press Enter.
The outcomes of the checksum could possibly be in distinction and verified with the anticipated outcomes.
When planning content material materials migrations, it’s essential to guarantee that recordsdata aren’t corrupted by the switch. Uncover one of the simplest ways to check and verify the integrity of files.